DDoS Simulation Testing
Verify your mitigation capabilities with the most realistic,
hacker-like DDoS attacks in a controlled environment.
DDoS Attack Simulation
Our testing service simulates deep multi-vector DDoS attacks:
- Volumetric attacks. Generating multi-gigabit attack traffic from multiple global locations, we test your ability to withstand extreme and sustained attacks with massive traffic, such as requests from a botnet.
- Protocol (network-layer) attacks. By generating protocol attacks such as SYN floods, UDP floods, and others, we evaluate how your network equipment (like routers, firewalls, and load balancers) can withstand attempts to over-consume resources.
- Application-layer attacks. We overwhelm your web server tier with excessive HTTP/S GET or POST requests that test your resistance to the more difficult-to-detect, layer 7 attacks, which target an edge server that executes a web application.
A Structured, Controlled Process
Using a “white-box” test methodology, we analyze your entire network architecture and decide on the most relevant attack vectors to test.
Planning Session
- Understand your network architecture
- Define clear goals, attack vectors
Controlled Attack
- Execute tests with 6-12 attack vectors
- Cover all attack categories (volumetric, application-layer, low-and-slow)
Report & Analysis
- Deliver test results
- Specify vulnerabilities and recommendations
Get Actionable
Recommendations
Following the DDoS Test, you receive a detailed report containing a full gap analysis outlining the main weaknesses, their severity, and how they should be fixed. Here’s a test report example.

DDoS Attack
Simulator Platform
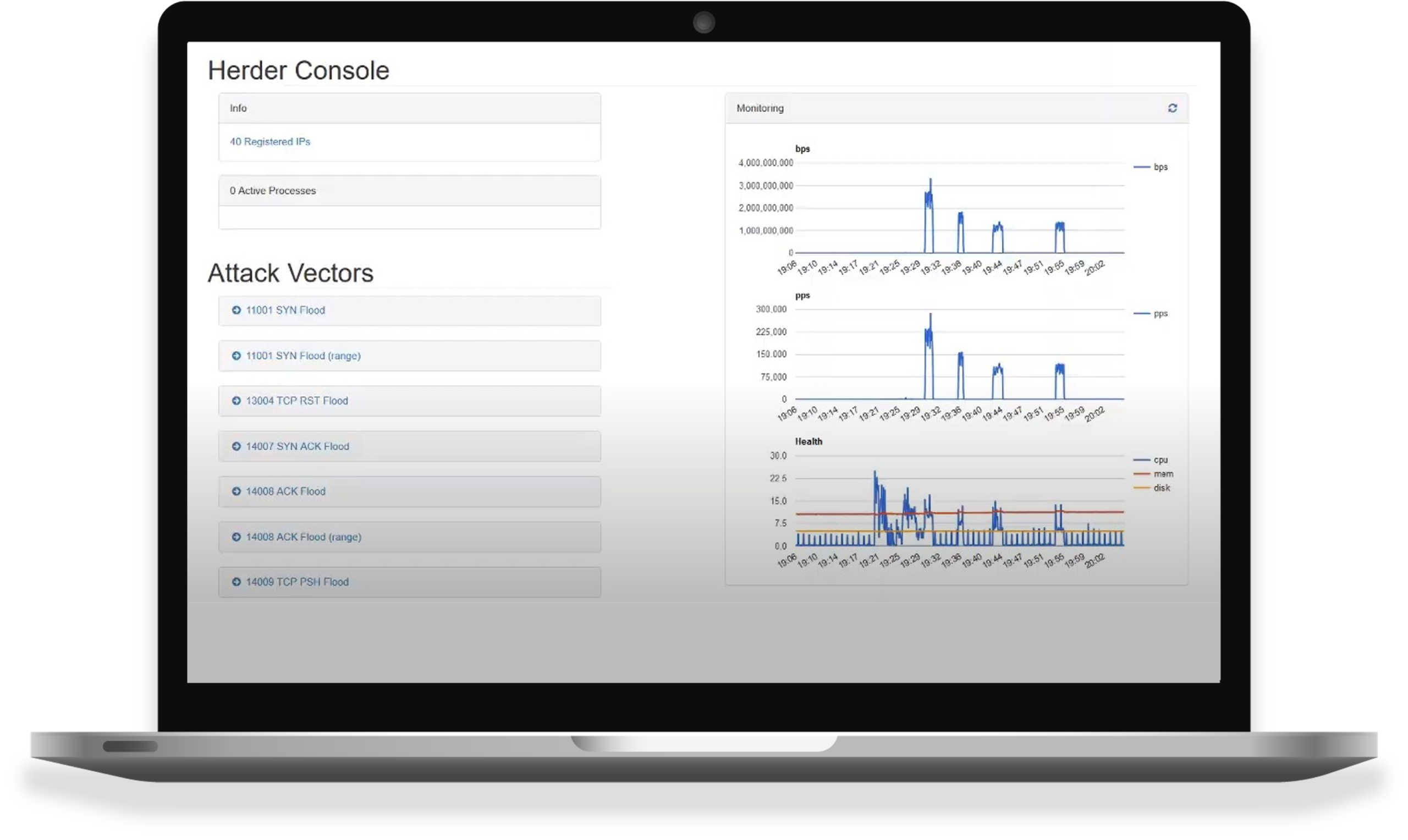
Our extensible testing platform executes DDoS attacks from bots distributed around the world. It sends real traffic using Web, DNS, and network attack vectors.
Test Options
Select the test option that best suits your needs, based on the number of attack vectors and duration.
Get in touch to find out more.
