There are several reasons. First of all, every digital environment must be tested to ensure full protection. DDoS protection without DDoS testing is like software without QA. Furthermore, while AWS assumes responsibility regarding network or infrastructure attacks, application attacks largely remain your responsibility. There are configurations and actions only you can perform, such as setting rate limits, scanner and probe protection, auto-scaling, and more. And all these application-level measures must, of course, be tested.
AWS DDoS Testing
Validate your system’s DDoS protection on AWS

DDoS Testing Tailored
to Your AWS Deployment
Verify your DDoS protection with attack simulations that challenge your specific deployment architecture. If your deployment includes CloudFront with ALB and EC2 behind it, for example, then we’ll run an attack simulation quite different from the one we’d plan if you had an API Gateway and AWS Lambdas.

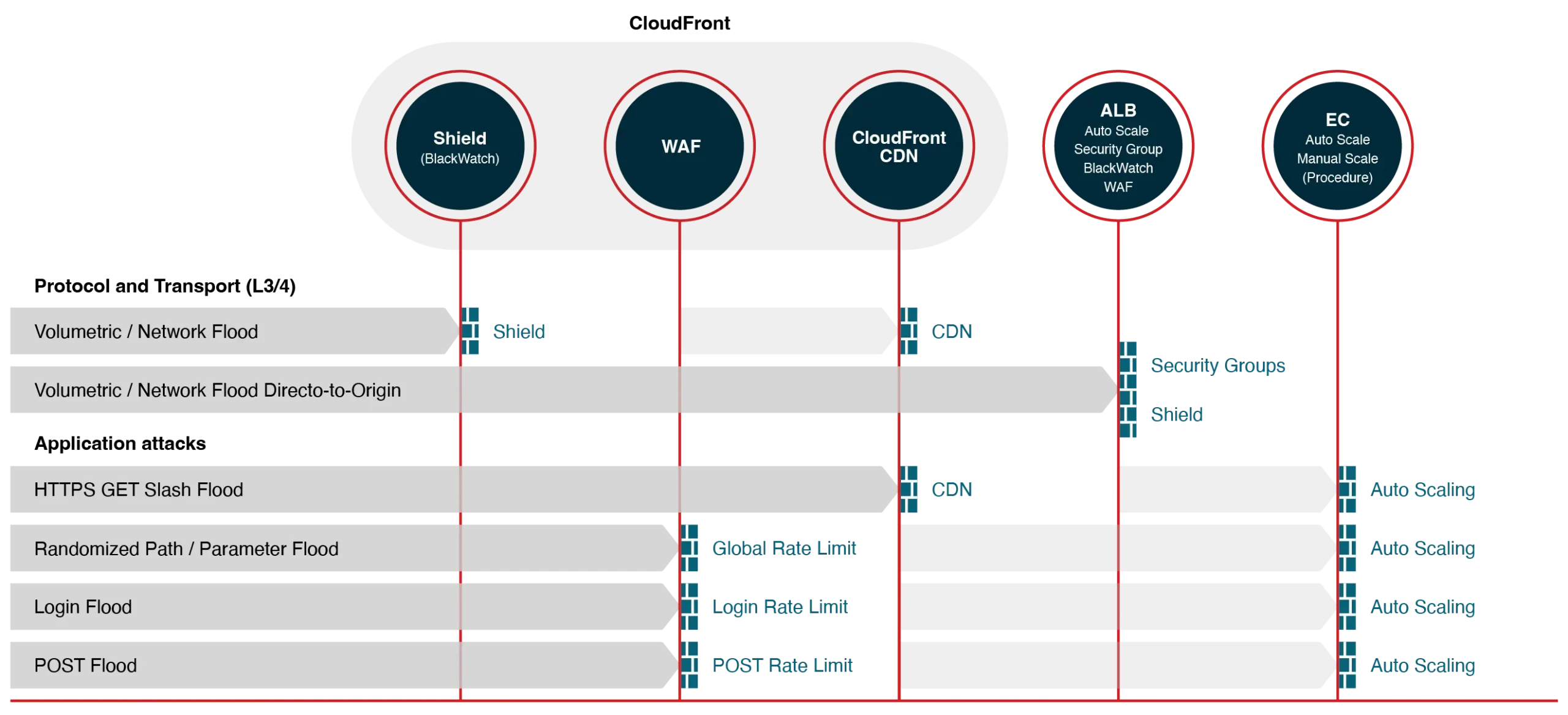
We simulate multi-vector DDoS attacks to identify which AWS component will (or will not) block each type of attack.
Actionable
Remediation Guidance
Following a DDoS simulation, you’ll receive:
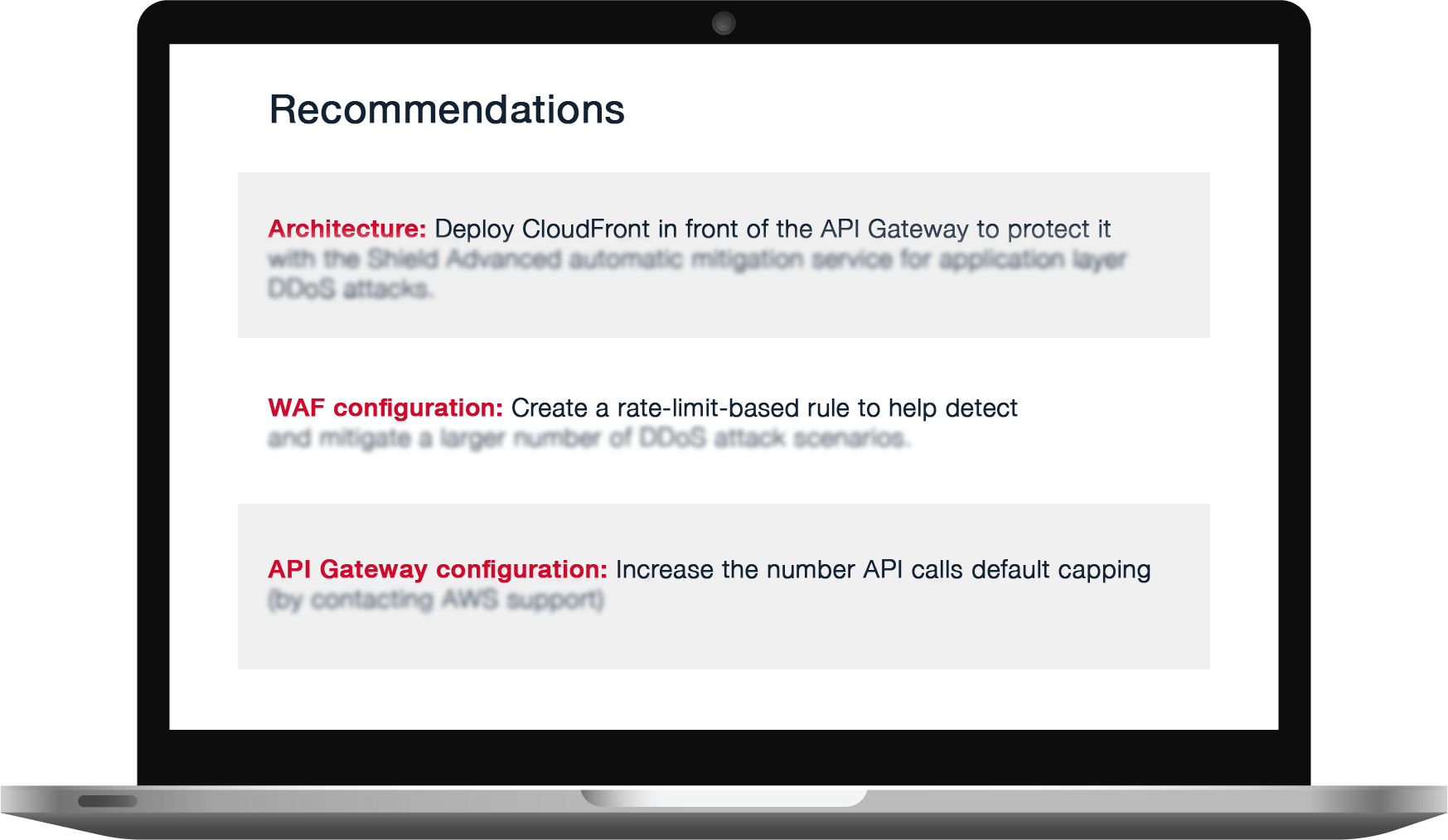
- A detailed report identifying all security flaws, prioritized by severity. (See a sample test report)
- Remediation recommendations – from optimal configuration of AWS WAF options to the addition of specific security components.
- An optional re-testing session to validate the fixes you implemented.
FAQ
No. Red Button can carry out DDoS tests without notifying the AWS team. This makes the process simpler in many cases, such as, for example, last-minute testing.
Yes. Our test simulation includes application-layer attacks that test your resistance to the more difficult-to-detect, layer 7 attacks; volumetric attacks to test your ability to withstand extreme and sustained campaigns with massive traffic; and protocol (network-layer) attacks such as SYN floods, UDP floods, and others.
The actual test simulation session typically takes three hours. A more extensive test simulation with more attack vectors can take up to six hours.
Yes. Following the DDoS penetration tests, we provide you with recommendations specifically tailored for the AWS platform. You can then decide to implement the recommendations as you see fit.
Yes. As a separate service, Red Button also provides support and guidance for implementing our DDoS mitigation recommendations.
