There are several reasons. First of all, every digital environment must be tested to ensure full protection. DDoS protection without DDoS testing is like software without QA. Furthermore, while Azure assumes responsibility regarding network or infrastructure attacks, application attacks largely remain your responsibility. There are configurations and actions only you can perform, such as setting rate limits, scanner and probe protection, auto-scaling, and more. And all these application-level measures must, of course, be tested.
Azure DDoS Testing
Ensure your Microsoft Azure deployment is secure with
simulated DDoS attacks in a controlled environment.

Tailored Simulation Testing
As an authorized Microsoft Azure Partner, we help validate your DDoS protection and ensure your services or applications continue to function as expected during an attack. We provide simulated controlled DDoS attacks, accompanied by a detailed analysis, and specific recommendations for improvement.
Our DDoS testing service, available to customers with an Azure DDoS Protection Standard plan, is customized to match your Azure deployment infrastructure. So, whether you use Azure CDN, Azure Gateway, or Azure Virtual Machines– we’ll test the attack vectors to maximize the value of your testing.
Realistic DDoS Attack Simulation
Using a controlled environment and bots distributed around the world, our testing team executes hacker-like DDoS attacks, to realistically assess your protection.
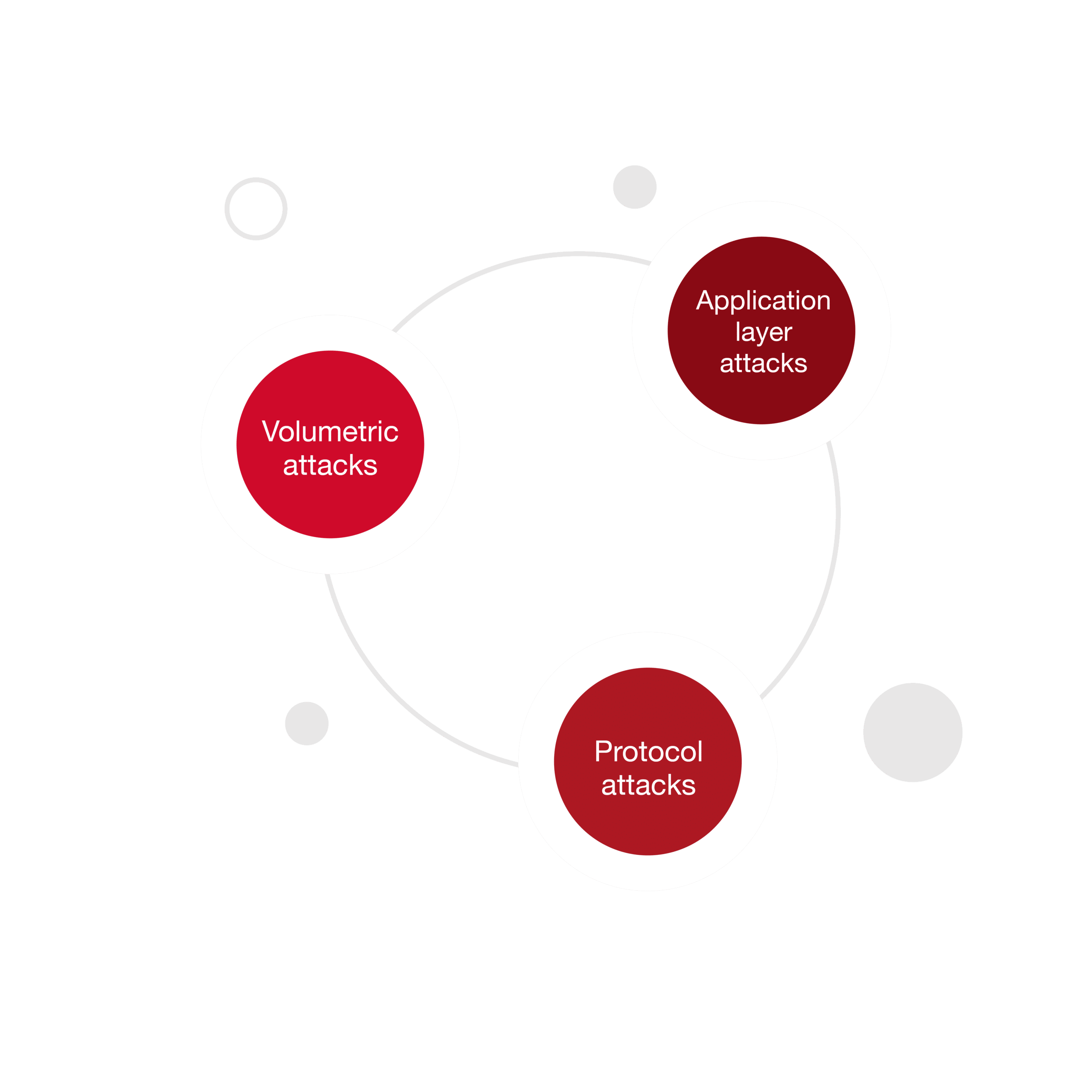
- Volumetric attacks. Generating multi-gigabit attack traffic from multiple global locations, we test your ability to withstand extreme and sustained attacks with massive traffic, such as requests from a botnet.
- Protocol (network-layer) attacks. By generating protocol attacks such as SYN floods, UDP floods, and others, we evaluate how your network equipment (like routers, firewalls, and load balancers) can withstand attempts to over-consume resources.
- Application-layer attacks. We overwhelm your web server tier with excessive HTTP/S GET or POST requests that test your resistance to the more difficult-to-detect, layer 7 attacks, which target an edge server that executes a web application.
A Structured, Controlled Process
Using a “white-box” test methodology, we analyze your Azure deployment infrastructure and decide on the most relevant attack vectors to test.
Planning Session
- Understand your network architecture
- Define clear goals, attack vectors
Controlled Attack
- Execute tests with 6 attack vectors
- Cover the relevant attack categories (volumetric, application-layer, low-and-slow)
Report & Analysis
- Deliver test results
- Specify vulnerabilities and recommendations
Get Actionable
Recommendations
Following the DDoS Test, you receive a detailed report containing a full gap analysis outlining the main weaknesses, their severity, and how they should be fixed. See a sample test report.

FAQ
No. Red Button can carry out DDoS tests without notifying the Azure team. This makes the process simpler in many cases, such as, for example, last-minute testing.
Yes. Red Button tests all DDoS attacks: network level, application level, low-and-slow, etc.
Testing typically takes 3 hours. A more complicated test can take 6 hours.
Yes. Following the DDoS penetration tests, we provide you with recommendations specifically tailored for your Azure deployment. You can then decide to implement the recommendations as you see fit.
Yes. As a separate service, Red Button also provides support and guidance for implementing our DDoS mitigation recommendations.