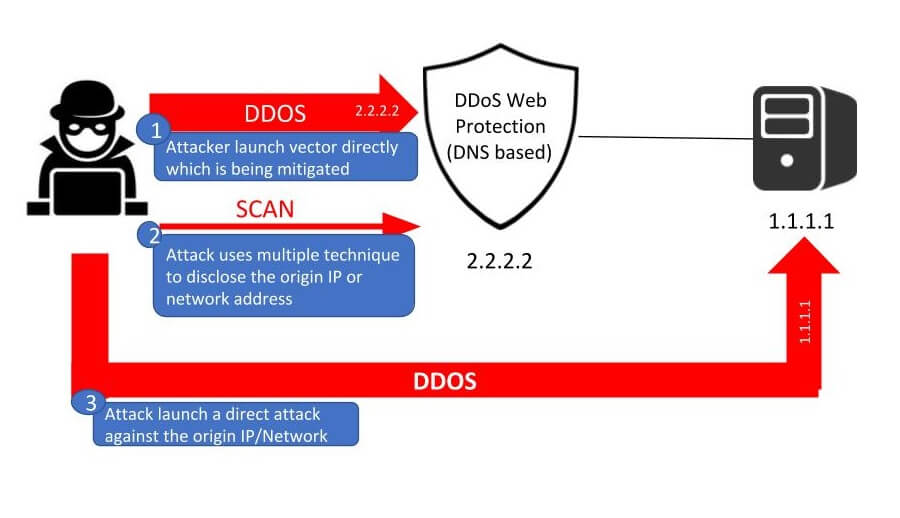
DDoS mitigation often uses an architecture using cloud-based protections, such as CDNs and WAFs. However, sophisticated attackers may attempt to reveal the origin network or IP address and attack directly, making the mitigation layer completely useless. This is typically referred to as an Origin Server DDoS attack or ‘Direct-to-Origin’ (D2O) attack.
This attack technique challenges organizations to either hide their sources (which is not always feasible), or mitigate the direct attack. For more information on how attackers expose origin server IP addresses and how to protect against an origin server attack, see this blog post.
The DDoS Resiliency Score (DRS) include this technique in attack vectors launched specified in ‘Level 6’ and ‘Level 7’.