Restructuring DDoS Protection of a Gaming Company on AWS
Background
As one of the world’s most popular online gaming companies, the organization is a prime target for DDoS attacks. The gaming company initially operated its own data center, where it implemented extensive DDoS protection mechanisms with the help of Red Button. For various reasons, the company then moved its data center to Amazon Web Services (AWS).
The Challenge
The move to the cloud required a complete restructuring of the company’s DDoS defense.
AWS provides two DDoS protection services: AWS Shield Standard (a free service) and AWS Shield Advanced – a paid service with additional detection and mitigation capabilities. While the company clearly needed the advanced protection service, it was still not enough.
The company’s security team wanted to ensure DDoS protection on AWS was at the same high level as it was at the on-premises data center. Achieving first-rate protection with full visibility, alerts, and an extensive defense against all types of attacks requires customer-specific setup, configuration and fine-tuning.
The Solution
Our expert team started with a thorough analysis of the company’s serverless system architecture to assess the full scope of DDoS vulnerabilities. Then, the following actions were taken.
Network-level Attack Mitigation
Preliminary analysis, which was later backed up by testing, indicated that AWS can block network attacks in both the AWS CloudFront (its CDN service) and the AWS ALB (its load-balancing service).
Application-level Attack Mitigation
The first line of defense against application-level attacks was established by defining rate limit rules in the AWS WAF (Web Application Firewall). Additional setup and configuration measures were implemented to handle ‘under-the-radar’ attacks, with low attack rates by each bot. To further protect against web application attacks, additional AWS managed rules were added, such as a core rule set (CRS), admin protection rules, known bad input rules, SQLi rules, and an Amazon IP reputation list.
Real-time Attack Visibility
An essential objective was to provide NOC and security personnel with real-time visibility into inbound traffic volumes and their effect, in order to better assess whether a DDoS attack was taking place. This was achieved by building a dedicated dashboard in CloudWatch (the AWS monitoring solution), with multiple widgets, presenting various metrics.
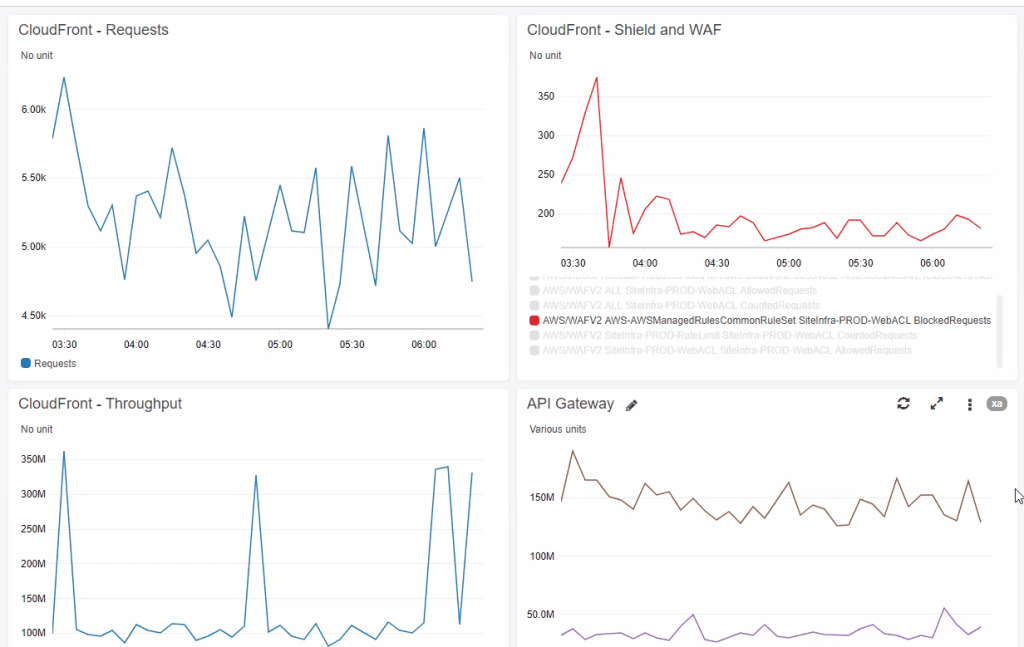
For example, the CloudFront Distribution widgets displaying inbound requests per second and the error response rate provide the data indicating whether or not an applicative DDoS attack is taking place. The Cache Hit Rate widget makes it possible to evaluate the degree to which the caching mechanism is blocking such an attack.
Any spike in these dashboards can indicate a DDoS attack. They provide the security officer with an understanding of the layers in which the attack is taking place, the nature of the attack (network or application), and whether or not it is being mitigated.
Automatic DDoS Detection
We implemented automated DDoS detection capabilities, including specific CloudWatch alarms to notify the relevant stakeholders about issues such as too many requests per second, a high byte upload rate, or a large number of errors.
DDoS Attack Analysis
Red Button tools provide unique, centralized insight to help better understand potential attacks. Using the external Kibana software, we created visualization dashboards that identify the attacked hostname or URL, query and payload parameters in HTTP requests, IP addresses of attacking bots, attack rates, and originating countries.
DDoS Testing
We then executed tests to reevaluate all the DDoS detection and mitigation capabilities, including the newly defined rules and threshold levels. This involved launching multiple application-level attack simulations.
Procedures and Training
Beyond technology, DDoS mitigation depends on the human factor. As our last step, we created a DDoS playbook containing written procedures for the NOC and security teams, and an e-learning kit for training new NOC members.
Read Other
Case Studies
Check out these resources for more information
about our DDoS testing solutons for your business.