Understanding DDoS Protection Topology Options
A DDoS attack is one of the more complex threats that businesses can face today. Given the complexity of attacks and IT infrastructures, an organization needs to adopt an optimal model to protect against a broad set of potential attack vectors.
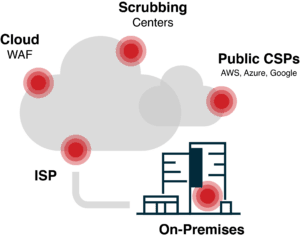
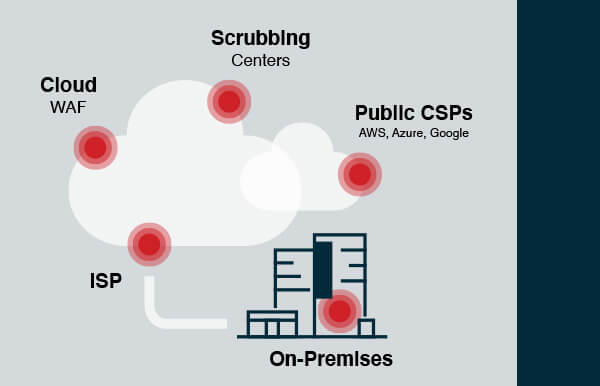
Essentially, there are 5 different locations for DDoS protection:
- On-premises
- ISPs
- Cloud WAFs
- Scrubbing centers
- Public CSPs (Cloud Service Providers)
Even before examining specific vendors, it is important to first understand each of the options – the topology, the type of DDoS attacks that can be blocked, and the advantages and disadvantages of each option.
Most organizations eventually have to combine two protection methods to effectively mitigate all types of attacks. I’ll discuss how to best ‘mix-and-match’ DDoS protection solutions in my next post. But first, let’s examine each of the protection locations.
On-premises
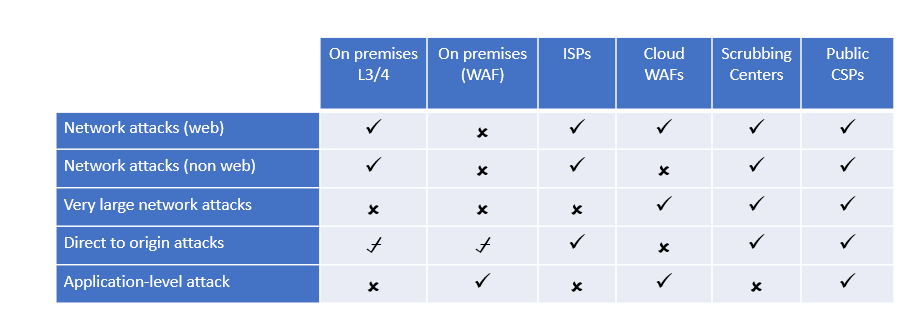
On-premises DDoS protection consists of a dedicated hardware appliance or an on-premises Web Application Firewall (WAF) installed within the data center. These allow an organization to protect itself against layer 3 and 4 network attacks (using a dedicated DDoS solution), as well as against application-level attacks (using the on-premises WAF) . Protection gear is installed at the network perimeter, between the internet router and network firewall.
The key drawback of on-premises protection is its limitation in blocking large DDoS attacks that are larger than the internet pipe. Meaning, if the network pipe is saturated due to the attack volume, the protection will simply not help. Another drawback is that WAFs were primarily designed to protect against network intrusion and data theft and therefore lack the scalability to block large-scale network and application-level attacks.
Overall, on-premises DDoS protection solutions have become less popular in recent years, with most organizations transitioning to cloud-based solutions.
Vendors offering on-premise DDoS solutions include Radware DefensePro, Netscouts Arbor Edge Defense, F5 ASM, and Imperva WAF.
ISPs
Many Internet Service Providers (ISPs) provide DDoS protection for businesses. The attractiveness of this option is clear – a very simple setup with hassle-free maintenance.
Yet, there’s a price. First, this option only covers network layer attacks and does not provide protection against application-level attacks. Another important drawback is that small and medium ISPs cannot stop large volumetric attacks. Very large ISPs, such as AT&T in the US, are an exception since they do have the bandwidth to absorb volumetric attacks.
Because DDoS security is not ISP’s core business, the expertise of the staff is typically lacking – something which you’ll only discover during an attack. This Imperva blog provides more information on the drawbacks of depending on an ISP for DDoS protection.
Cloud WAFs
With the migration of applications from the private data center to the cloud, cloud-based DDoS protection solutions have gained popularity over on-premises solutions.
Cloud-based DDoS protection is based on companies offering CDN and cloud WAF solutions, which also include a DDoS mitigation layer. Traffic is diverted using DNS to the cloud provider, which can easily handle large volumetric attacks. Because the original server is not the one responding to requests, it’s much harder for any DDoS attack to reach the attacked server.
Cloud WAFs also protect against application attacks, both static and dynamic. The one attack vector that cannot be blocked by cloud WAFs is Direct-to-origin attacks.
Cloud WAF DDoS protection is easy to deploy and maintain. It does require the organization to provide the private keys to the web provider, which in some cases, such as governmental entities, may be an issue.
Vendors providing cloud DDoS protection include Akamai, Cloudflare, Imperva (Incapsula), and Reblaze.
Scrubbing Centers
A DDoS scrubbing center holds DDoS mitigation equipment that can handle large-size network attacks. Most vendors offer a solution consisting of multiple scrubbing centers, typically distributed globally. During an attack, traffic is diverted to the closest scrubbing center, where traffic is analyzed. Malicious traffic is removed, and only legitimate traffic is passed to the company’s network.
Customers can make use of scrubbing center protection in two ways – either route traffic on demand when an attack occurs, or else route traffic via the scrubbing centers at all times.
A scrubbing center can stop any type of network attack, both web, and non-web (FTP, SMTP, etc.), as well as direct-to-origin attacks. However, it cannot provide protection against application-layer attacks.
Compared to Cloud WAF protection, the implementation of a Scrubbing Center solution is more complicated due to the BGP traffic diversion and GRE tunneling. It requires an organization to own an autonomous system and network classes, but on the positive side, private keys are not needed, like in the Cloud WAF solutions. Another issue that may arise with a scrubbing center is latency.
Vendors providing scrubbing center solutions include Radware, Arbor, Akamai Prolexic, F5 Silverline and Cloudflare Magic Transit.
Public CSPs
Public Cloud Service Providers (CSPs), such as AWS, Microsoft Azure, and Google Cloud, provide DDoS protection as part of the hosting service.
CSPs typically provide network protection as an ‘out-of-the-box’ service that is part of the hosting package. Responsibility for network protection is on the CSP, and as a customer, your DDoS protection enjoys the built-in scalability inherent in the cloud data services.
Application-level protection, on the other hand, is charged separately. Essentially, this is a built-in Cloud WAF solution provided by the CSP, where the configuration and ongoing management are your responsibility. At the time of writing this post, CSP-based application protection is less mature or sophisticated than the cloud WAF vendors that provide a point solution. Clearly, the convenience of having all DDoS protection under a single roof is valuable.