Large File Download: A Sneak DDoS Attack

Your website most definitely has files that can be exploited by hostile adversaries to take the site down without you even noticing that it’s happening – until it is too late.
What is this “invisible” sneak attack?
It’s known as a large file download attack – and it can be quite harmful. Also known as an outbound pipe saturation, it is a clever asymmetric application-layer (L7) attack that uses multiple continuous requests to download a large file found on the targeted website or server. The result is a network data pipeline clogged with outgoing traffic until it can no longer bear the load, leading to high latencies or even downtime.

Large File Downloads Fly Under the Radar
Attackers can find downloadable files for exploitation on almost every website. These can be PDFs, text files, software updates, OS images, databases, application data, graphics, media, JavaScript assets, or other objects, some as small as 1 MB. The large file download attack is relatively simple, directly targeting the server where these files reside. But what makes the attack so effective and underhanded is that it flies under the radar of common DDoS mitigation techniques.
The rate of malicious requests is kept low enough to avoid triggering a response by the web application firewalls (WAFs), which are supposed to detect and mitigate application layer attacks. That makes large file download attacks initially very confusing. The site is not operating as it should, yet no alerts are triggered because no rate limit has been violated. IT security teams may even initially assume they are merely seeing a jump in legitimate requests clogging the line and it can take hours just to identify that a DDoS attack is underway.
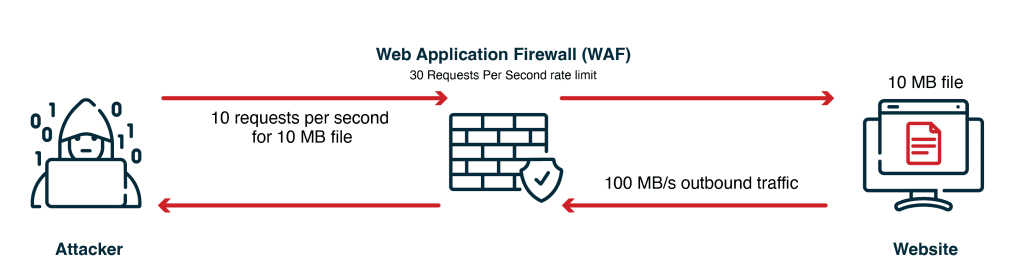
Low-rate requests for file download are difficult to detect as they are below the WAF rate-limit threshold
Even a smallish network of 300 bots – and we see botnets of thousands nowadays – can be set up to easily bypass WAF configurations by keeping each bot request rate below the threshold of the rate limit rule. During recent simulations Red Button carried out for two customers, targeted websites were taken down very quickly with very little effort with large file download attacks. In fact, the larger the downloadable file is, the easier it is to exploit with fewer requests and smaller botnets.
How to Mitigate Large File Download Attacks
- You’ve already taken the first step: Be aware. Once you know to look out for large file download vulnerabilities, you’re better positioned to adopt the appropriate mitigation measures and identify an attack when it happens.
- Remove unnecessary files on your server or website. Identify any large files in your system that are not actually needed. You may be surprised to discover large unused files on your servers that expose you to unnecessary risk.
- Set distinct rate limits. It is nearly impossible to set general rate limits that are low enough to prevent pipeline saturation by large file download attacks without also blocking legitimate traffic to your site. However, you definitely can configure a distinct request threshold for the specific pathways leading to your exposed large files. Bear in mind that most websites are fairly dynamic, with files moved from their locations or webpages getting periodically reorganized. If file pathways are revised, then their associated rate limits need to be once more configured accordingly; otherwise, the website is again open to easy large file download attacks.
- Setup and configure a CDN. A CDN is the most effective solution for mitigating large file download attacks. Malicious requests end up getting the file from the CDN cache, which responds using its distributed network of servers, preventing any impact whatsoever on your network pipelines and servers.
- Ensure caching cannot be bypassed. There are a few known tricks of the trade that attackers might use to bypass the CDN cache (such as fooling the CDN into thinking each request is the first one, which is sent directly on to the large file’s location for download). Consult with your vendor to make sure your CDN has mitigation measures and thresholds in place to identify and prevent such cache hacks.
- Activate your DDoS protection technology’s built-in large file download features. Your DDoS protection technology vendor may offer tailor-made large file download protection features, such as F5 Advanced WAF. They may also incorporate best practices for identifying and mitigating such attacks in their standard or advanced services.