68% of Companies are More Vulnerable to DDoS Than They Think

As everyone in the security space knows, misplaced confidence can often be much worse than a known weakness. When you have an accurate idea of where your vulnerabilities are, at least you can focus your mitigation resources there accordingly. But if you think your defenses are strong where they are not, or you don’t truly understand the adversary’s capabilities, then you will always misallocate your forces and leave yourself open to attack.
Unfortunately, that is almost always the case when it comes to DDoS protection.
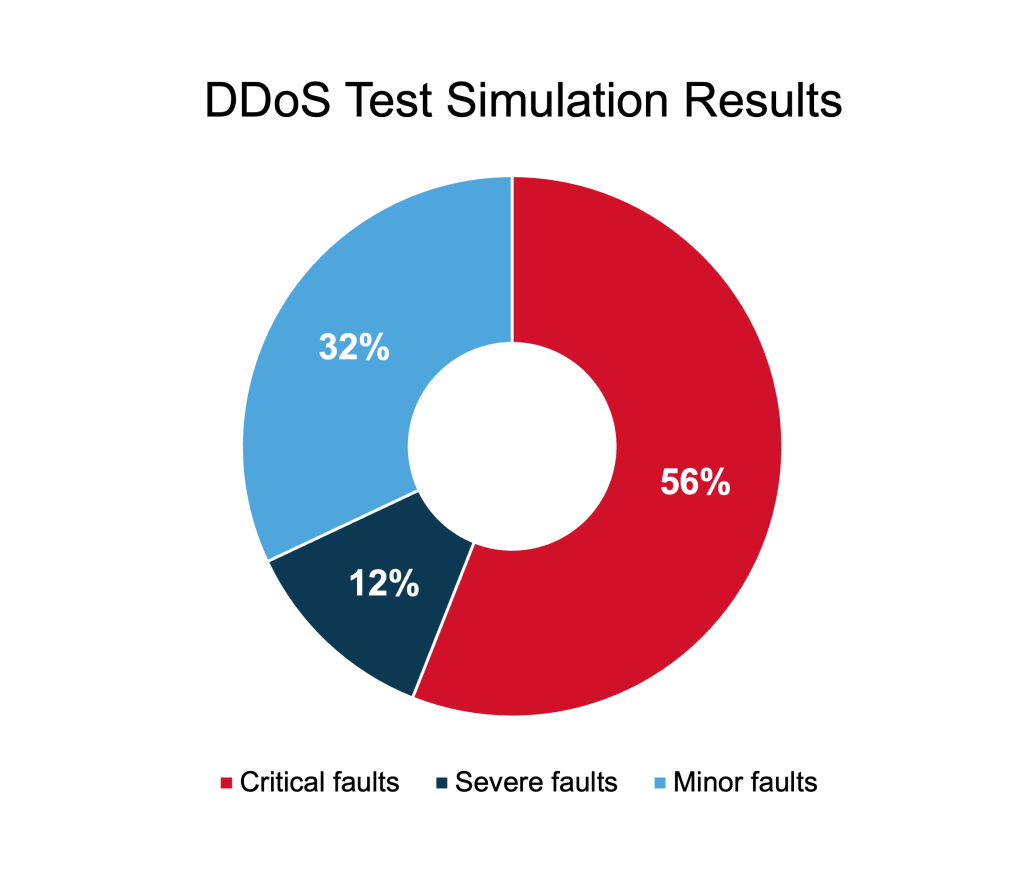
Our experience has shown that a large majority of companies are more exposed to DDoS attack than they think they are. The DDoS attack simulations we ran in the last quarter identified excessive vulnerabilities across industries and organizations of all sizes. Sixty-eight percent of the protection faults uncovered by our simulation tests were either severe (i.e., no detection or mitigation of an attack) or critical (i.e., only partial detection/mitigation).
Accurately Assessing Your DDoS Security Posture
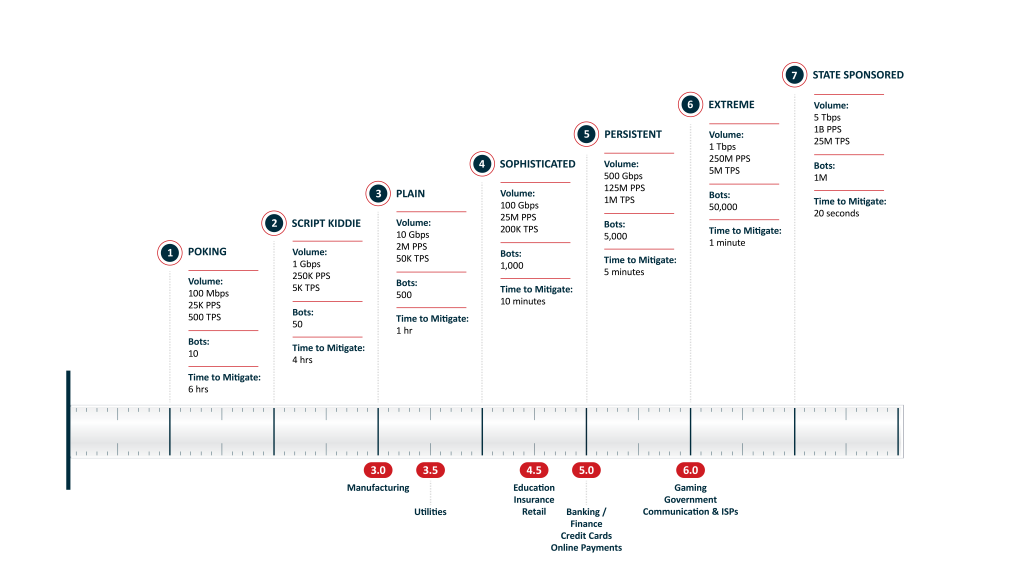
The DDoS Resiliency Score (DRS), developed by Red Button, is an open standard providing an objective yardstick for quantifying an organization’s ability to withstand DDoS. It defines seven ascending levels of attack, each one introducing additional sophistication, vectors and traffic volumes. Similarly, the requirements on the defending side increase, with each level requiring a shorter mitigation response time.
It is important to note, however, that different industries face different levels of threat. Based on real-world data, the finance, communication and gaming industries, for example, are among those prone to the most sophisticated DDoS attacks.
The following chart indicates where various industries fall on the DRS threat scale, which naturally creates a benchmark for adequate protection in each sector. It allows you to evaluate what kinds of DDoS attacks your specific organization should normally be able to withstand.
The (Surprising) Results Are In
The problem is that most companies are completely unaware of both how much protection they need and how protected they actually are. That’s why they are so often truly surprised by the results of initial DDoS attack simulations.
A bank leadership team, for example, was shocked at the results of a DDoS attack simulation we conducted. While the bank’s system was able to partially mitigate standard network attacks (SYN, ACK and UDP floods), it failed to identify or mitigate the first, basic application-level attack simulation, to the point that we decided not to continue with additional tests. After receiving our DDoS report, the senior CISO commented, “Without seeing this conclusive analysis, I would never have believed this was our status.”
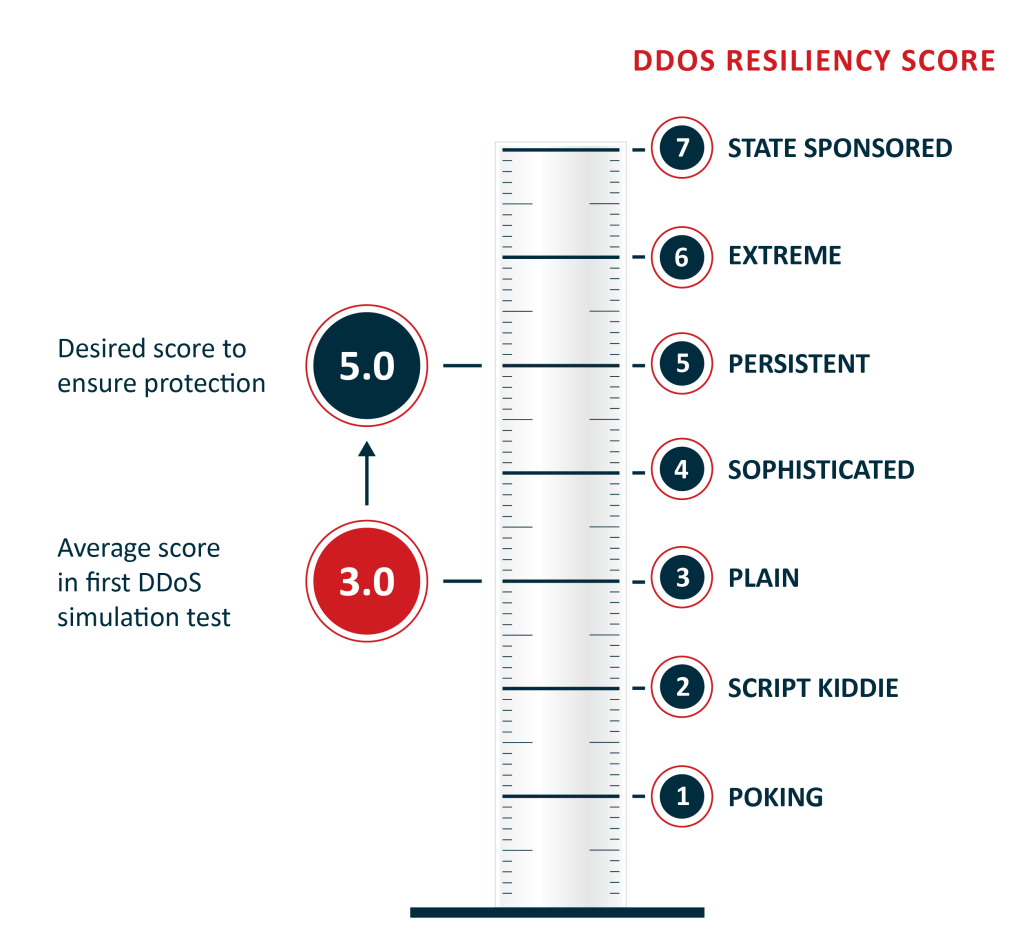
The average DRS score Red Button has seen during initial DDoS simulations is around 3.0. The problem is that the average recommended score, based on known and expected threats, is between 4.5 and 5.0. This is a major disparity, indicating a high risk of significant denial of service in the event of the most commonplace attacks.
Why Is This Happening?
There are several reasons a company might not be properly aligned to effectively mitigate DDoS attacks. They can be summarized under three main headings.
- Technology: Companies need to obtain the latest available DDoS mitigation and digital asset protection technologies available. But that is not enough. In our experience, companies often fail to configure and fine-tune their solutions to meet their specific needs, which can undermine even the best of efforts.
- Responsibility: Many companies believe they are sufficiently protected from DDoS attacks by a third party, generally their service provider. In reality, however, this reliance is only partly justified. They are unaware of their role and the shared responsibility they have with their service provider in ensuring online assets are secure.
- Training: Even with the best approaches to tech and collaboration, the human factor is still irreplaceable. Companies sometimes discover that their IT teams are woefully unprepared for an actual DDoS campaign. They need to be trained and a DDoS response protocol should be written, followed, and refreshed or updated periodically. Otherwise, the ability to mitigate an attack of any sophistication will be severely compromised.
As a character in The Newsroom famously said, “The first step in solving a problem is recognizing there is one.” It’s well past time to learn that lesson about DDoS security now. The costs of delay can be far too high.