DDoS Testing
Controlled and safe DDoS attacks to evaluate your defenses and uncover problems, so we can provide targeted, actionable recommendations.
We help banks, financial organizations, gaming companies and high-risk orgs
prevent and mitigate DDoS attacks.
There are three key reasons why DDoS attacks succeed, despite large expenditures for DDoS protection technologies.
Controlled and safe DDoS attacks to evaluate your defenses and uncover problems, so we can provide targeted, actionable recommendations.
Analysis of your technology infrastructure, with detailed recommendations for network architecture improvements and configuration optimization.
Year-round activities to protect at-risk companies, including periodic DDoS testing, technology hardening, training, and incident response.
Tailored, hands-on training to increase the skills of your security and IT teams, so they can quickly identify and respond to attacks.
Our Incident Response (IR) team handles critical DDoS emergencies, efficiently and effectively stopping the attack and minimizing downtime.
1000+
DDoS tests performed
250+
Worldwide customers
150+
DDoS attacks mitigated
Red Button is an authorized DDoS Test Partner of both AWS and Microsoft Azure.
Your team is extremely professional and dedicated. They are so committed - no less than my own employees – that it sometimes feels like we’re their only customer."
I would like to thank you for the major efforts of your team during the last 36 hours, helping us handle a DDoS ransom threat and harden our systems."
You guys are amazing in every way. Your open-minded approach is your key strength. You listen to your customers and always challenge the status quo with making your DDoS toolset even better.
Your DDoS attack simulations were much stronger compared to others - both from the scaling factor and how fast you can stop and start them.
Outstanding. Kudos on the amazing team and work!
Your DDoS experts are amazing individuals who are very informed. They deserve a lot of kudos.
- We love working with your team. Work is very professional.
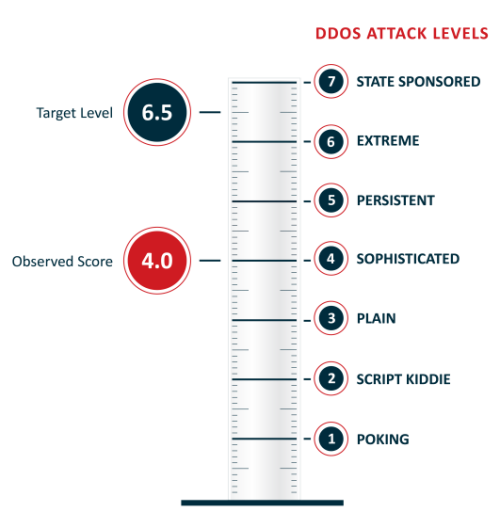
The DDoS Resiliency Score (DRS) helps you evaluate your DDoS attack risk, understand the type of attacks should you be able to withstand, and compare your protection level to other companies in your industry.