| Family | Network Attacks |
| Attack Vector | UDP Flood |
| Variants | Reflective Amplified FloodsDNS Garbage FloodUDP Port 80 Garbage Flood |
| DRS ID | 22003 |
| Supports spoofing | Yes |
| Capture file example |
Description
A UDP Flood is a network DDoS attack involving the sending of numerous UDP packets toward the victim. This attack can arrive from a spoofed source IP address; it does not require opening a connection, which is the reason why an attack can generate massive amounts of traffic with few resources.
UPD will, foremost, cause internet pipe saturation. It can also impact firewall and other stateful devices.
UDP flood is actually a family of many attack vectors, including virtually all the reflective amplification floods, the DNS garbage flood, the port UDP port 80 garbage flood and more.
Impact
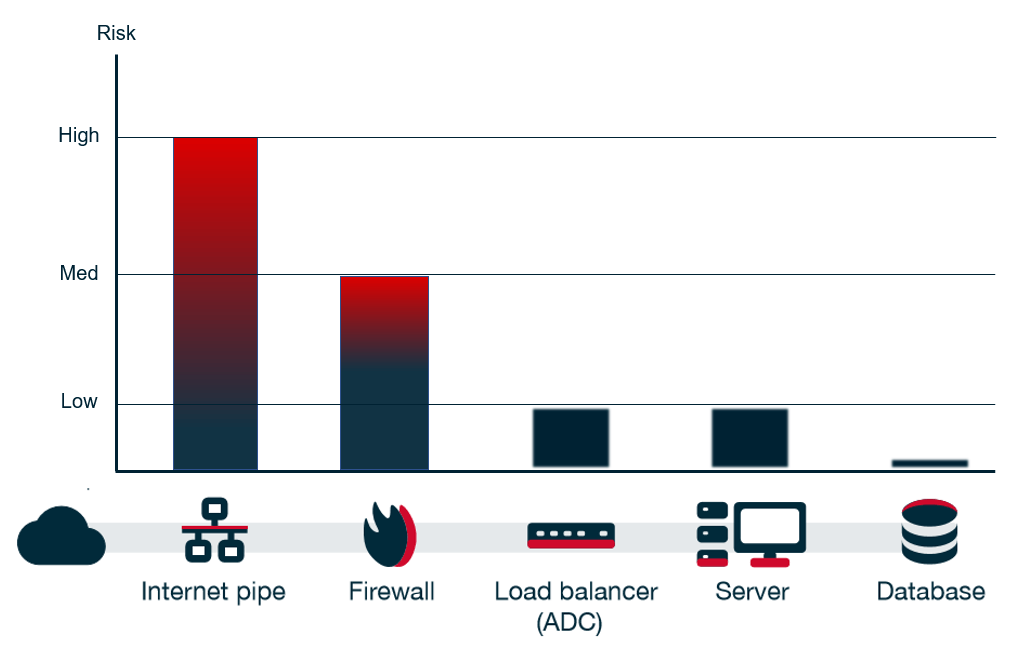
The UDP flood’s main objective is to impact the internet pipe. Attackers today can easily generate floods at rates of 1Gbps, 10Gbps, 50Gbps and more. Most organizations have lines less than 1Gbps.
If the line is not impacted, the firewall or other stateful devices can be overwhelmed by the attack since they must allocate resources to each of the packet’s.
Mitigation
| Technology | Description |
| Challenges | |
| Proxy | ✔ |
| State/Anomaly protection | ✔ |
| Caching | |
| Rate limit | ✔ |
| Signatures | |
| Behavioral | ✔ |
*UDP floods are typically mitigated